Social media policy in law enforcement is a hot topic and well it should be. No one can or should dispute that the importance of sound policy, and the need to guide law officers in proper behavior and procedure online, is huge. Just when you’re getting a handle on the elements of a good social media communication policy, and you’re thinking your social media investigations need to be covered by policy as well; if you’re vetting potential new officers on the Internet, you’ll need a third policy for cyber-vetting of new recruits too. I’m no HR professional, but the legal ramifications in this area could be gigantic. This post is an overview of some important considerations for all three social media policies.
Social media policy in law enforcement is a hot topic and well it should be. No one can or should dispute that the importance of sound policy, and the need to guide law officers in proper behavior and procedure online, is huge. Just when you’re getting a handle on the elements of a good social media communication policy, and you’re thinking your social media investigations need to be covered by policy as well; if you’re vetting potential new officers on the Internet, you’ll need a third policy for cyber-vetting of new recruits too. I’m no HR professional, but the legal ramifications in this area could be gigantic. This post is an overview of some important considerations for all three social media policies.
Slightly less than a year I wrote for the first time on social media policy in law enforcement. Much of what should be in a law enforcement social media policy (copyright, fair use, truthfulness, and the like as covered in the original article) is in every good social media policy. I especially like the policies of the Air Force, IBM, and Intel. But while that’s true, there are several areas that are unique to law enforcement. These were also covered in my original article. I offer here a couple of new insights.
1. Communication Policy / General Use
I have added two items (#8 & #9) to the list of areas unique to law enforcement since writing the original article, but haven’t changed the rest.
- Integrity. Perhaps the most important part of everything a law enforcement agency does online or elsewhere is integrity. Agency participants in social media should be reminded that Integrity is the essential ingredient to using social media ethically. Agency employees should, therefore, be honest in their use of social media and maintain high regard for the public interest. All information disseminated should be absolutely accurate.
- Disclaimers. Because you may be giving your personnel the authority to comment on issues relating to the department, it’s imperative to emphasize the importance that officers, especially, state that what they write is their own opinion and not that of the department.
- Identity. Some bloggers work anonymously, using pseudonyms or false screen names. Law enforcement agencies should absolutely insist that in blogs, wikis or other forms of online participation that relate to the department or the city, or activities or issues with which the department is engaged; department employees use their accurate identity.
- Department-sanctioned tools. While it should be stated that the social media policy of the agency covers activity by agency employees on tools they may create on their own or those of others that they might contribute to, department-sanctioned tools should be governed more closely. Careful distinction needs to be made between on and off duty work online.
- Competence. Department employees, whether staff or sworn, should not use any social media tool unless they really understand how it works. Many of the problems with officers getting themselves into trouble happen on Facebook and often the officer(s) involved indicate they didn’t know Facebook worked the way it does. Make your staff responsible for assuring their competence online.
- Command Staff responsibility. Standard disclaimers, do not by themselves, exempt command staff officers from any special responsibility. By virtue of their position, they must consider whether personal thoughts they publish may be misunderstood as expressing opinions of the agency.
- Training. Provide social media training for your officers and staff. Once your policy is written, be sure to distribute it with conversations about departmental support for social media.
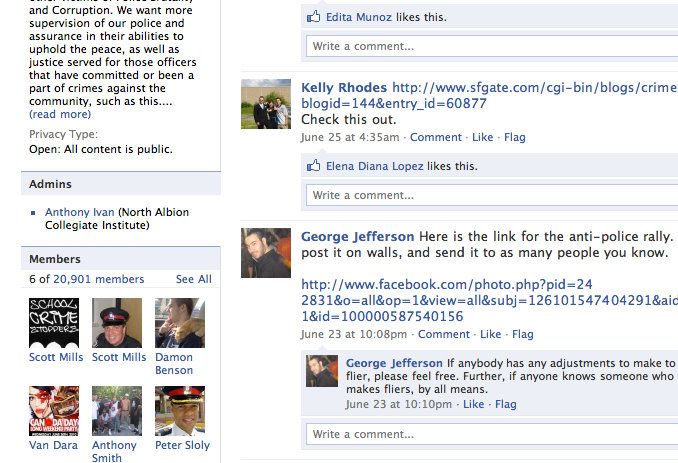
- What’s not o.k. to post. This may include things such as department identification (patches, insignia, officers in uniform) and sensitive information or any other information that could reflect negatively on the department.
- Implications on career. All violations of policy or misbehavior online could have detrimental effects on an officer’s career. But one that doesn’t seem obvious to all is the effect simply having a social media profile, even if there’s never a problem, could have on an officer’s future ability to perform undercover work. Tremendous care is warranted so than an UC officer can’t be intified online.
2. Cyber-Vetting Policy
-
Notice and Consent
- Informing applicants It’s absolutely essential to let applicants know that you’ll be conducting a search of their social networking profiles. Your policy should state that they will be told and at what point in the process they will be told. Some agencies don’t want to give them a lot of notice so the profiles don’t get altered, but surprising them altogether may not be fair.
- Consequences of not giving consent Consent needs to be given to search a person’s online profiles, especially if the agency expects to search password-protected sites. The applicant should be told that not giving his or her consent could disqualify him or her from consideration.
- Type of information investigator may collect Will it be ok for your agency to speak with the online friends of your applicants? Some people are really taken aback by this but is it different from visiting their neighbors? Define circumstances under which agency may contact online friends and otherwise define of the scope of the search, inform the candidate, and consistently apply it to all applicants.
-
Quality Assurance & Training
- Internet search training for investigators The world of online media is complex. Investigators need to understand the nuances of privacy settings, imposter pages, gathering and storing of evidence.
- How they’re monitored
What procedures are in place to make sure the investigator is operating professionally and securely? - Ongoing refresher training
Because platforms like Facebook changes the rules regularly and because there are always new platforms of which you need to be aware, make sure the investigator attends training at regular intervals. -
Internet Search Practices
- Who can conduct searches?
The answer is definitely, positively NOT – “the intern”. That seems obvious to most but it’s happened. The procedure for determining personnel authorized to perform such searches needs to be defined as well as the ongoing method by which one will be qualified to remain authorized. Should this position be defined as sensitive and receive all the protections therein? - Outline expectation for notification of changes
Do you want to go so far as to require employees to notify you of any changes to their online profiles, such as new profiles they might have? - Disclosure of blogs they own or on which they participate
Consider making it policy that if an officer starts a blog or begins to contribute to one, s/he should disclose it first. Also state your position on the prospect of posting anonymously. - Email addresses
Applicants should provide email addresses that they have used in the past. Law enforcement generally agrees an email address is an important search term. Issues here include the applicants memory of all email addresses, or those used for undercover or sensitive work. - Disclosure of online identity
Many agencies are asking applicants to list current screen names and nicknames used online. What happens if they disclose bank account username/password (because it may be the same as that used for a social platform) and then something happens to that account? Or their identities are stolen. Can they come back and blame your agency? - Command Performance
Many agencies are opting to have applicants open up their password-protected sites during the face-to-face interview so that decision makers can review online content during the face-to-face interview, sometimes without warning. Applicants should be afforded the opportunity to explain any online information. - Limited to a workplace computer
Authorized personnel conducting Internet searches for employment or security clearance purposes may review online information from publicly accessible, unrestricted websites. - Use of applicants social security number in searches
There are many inherent dangers to the practice of putting someone’s social security number in an online search. Doing so can make it viewable to others. It isn’t recommended to be done on social sites which index content. - Misrepresentation
Circumstances under which misrepresentations will be made to obtain online information need to be defined. Besides being in potential violation of social network’s terms of service, this topic is controversial. You create fake profiles to catch pedofiles, but under what conditions, if any, would you consider creating a fake profile to investigate a potential employee - Wall-off
Some law officers have indicated they feel that if someone discloses potential protected-class types of info online it’s equivalent to a waiver of their privacy. That doesn’t mean a judge would agree. A wall-off procedure needs to be in place to protect the applicant and the hiring manager regarding Internet search results pertaining to protected classes (e.g., age, sexual orientation, race, etc) so that the hiring manager doesn’t see information falling within the definition of protected class. - Criminal Evidence
When/if criminal evidence is uncovered during a cyber-vetting procedure, what is done with the evidence? -
Monitoring & Reporting After Hire
- Ongoing monitoring
Employees should be informed if it is the agency’s intention to monitor their activities online. - Conditions for ongoing monitoring
In response to specific concerns, complaints, or information about an employee, organizations may conduct online searches to obtain additional information on that employee. - Reporting by peers
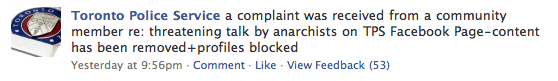
Should an employee who becomes aware of an Internet posting or Web site that is in violation of the organization’s policies report the information to a supervisor. Are anonymous reports o.k? - Accountability
Employees shall be responsible for ensuring that sensitive information is not posted on their family members’ social networking sites. - Rebuttal/Defense
Employees should be given the opportunity to address anything negative found online. It could be the work of an imposter or an angry ex-spouse. Is the employee allowed to have a copy of the evidence? -
Application of Internet vetting findings
- Employment decisions
Hiring, retention, promotion, security clearances and disciplinary decisions, based at least in part on the results of an Internet search, must be based on established criteria and processes. - Security
How are the results of Internet searches stored and protected? For your own protection as well as that of the candidates, establish conditions under which the results of your investigation is destroy or stored, and for how long. On the one hand, you may not want it around for liability reasons, on the other if you deny employment to someone, you may need the evidence to prove your negative decision was NOT discrimination.
Some or all of the points in this section could also fall under the “general use” section above.
3. Investigations Policy
I’m not a trained investigator but I offer a few points here only to the extent social media platforms are involved.
- False identities
Give proper consideration for the procedure by which you will obtain false identities and take into consideration the workings of each platform.
- Department only equipment
The use of department-only equipment which has no online identifiable ties to the agency. This is standard in any investigation but take special consideration for the use of mobile technology, especially geo-location enabled. - Training/Competence
Always important. There’s always a new tool, sometimes a very simple one that will benefit your agency. Keep your investigators well trained and don’t underestimate the value of training by professionals who genuinely live in the world of social media. Any cyber-investigator knows how to put up a false profile, but examine whether your trainer really is up-to-date on the very latest technical developments in the social world. Include in your policy that training is to be provided and investigators need to take on responsibility to know what they don’t know and learn it. A good cyber-investigator stays up to date him or herself by tuning in social media blogs and other sources. - Proper documentation
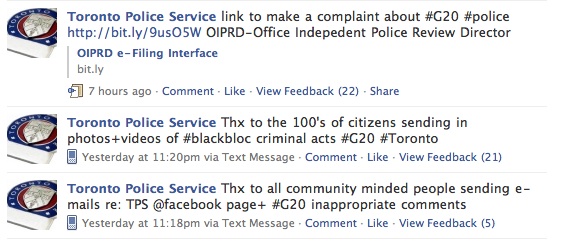
The technique of gathering of anything online should be treated with great care. How it was obtained, with date-stamp, in the chronological order it was obtained is of upmost importance. And, with social networks, the content itself changes quickly. Evidence needs to be gathered more quickly than may have otherwise been necessary, don’t lose sight of the need to document carefully. - TOS violations
Some investigative activity is technically against the Terms of Service for social networking platforms. Know the TOS statements of the platforms you’re using and put into policy under what circumstances your agency will conduct activity which may otherwise be in violation of those TOS.
Three final thoughts:
In addition to the specific points above, there are some themes that transcend all policy development in social media.
- Consistency
One of the biggest arguments for social media policy is so that your agency can be sure that personnel are all treated equally. If you’re accused in court of discrimination in a hiring decision and you don’t even have a document to present that shows you intend to perform fairly for everybody, that’s a big piece of potential protection missing. Of course, actually practicing consistency goes hand in hand with saying you do so. - Training/Competence
Training and competence are not the same. I regularly see and hear policy personnel saying training should be part of all policies. But just because training is provided, doesn’t mean the trainee is competent with the tools. I recommend putting the onus on the employee to be able to assure his or her thorough knowledge of the platforms s/he is on regardless of purpose. A great majority of the cases where an officer gets himself into trouble – especially on Facebook – with career ruining activity, could have been prevented if the players had better knowledge of how the platform worked. So provide the training, but include separately that they will held accountable and that blaming mistakes on not knowing it would happen won’t be tolerated. - Honor your agency’s culture
No matter what you read or who you talk to, always honor the culture of your own organization when developing policy. If your agency doesn’t need to be overly restrictive and punitive with social media, especially with regard to how you expect sworn officers to behave when representing the department, you will know it. Moreover, the agency will benefit because the officers won’t feel like it’s just not worth doing because it’s too easy to get into trouble.
It’s a brave new world we live in. The main thing is to go forth without fear of these media. There’s more benefit than risk and sound policy will go a long way towards protecting your agency in the online world as well as allay fears that you’re not ready.
As with this or any other post on ConnectedCOPS, let me know your thoughts via the comment section below or get in touch any way you prefer.