Hacks mimic identity of your friend to access your information
 Friends connecting on Facebook, more than ever, is something that needs to be respected and trusted.
Friends connecting on Facebook, more than ever, is something that needs to be respected and trusted.
Recently a number of people including me have received friend requests on Facebook from people they know. Why is this unusual? Because these requests are from people who are ‘already’ connected and listed as friends.
The requests are from scammers attempting to gain access to your Facebook account and utilise your information that you share only with friends. They are using the scam of Ghost Accounts. Meaning they are Fake Imposter Accounts, that have copied everything from a friends Facebook Account, that is available on public view.
Once they are accepted into your account, they are in a position to glean as much information as needed to further their scam. They send friend requests to your friends and can make an imposter account from your details.
What to do
If you receive a request, firstly check with your friend to see if they have created another account.
If they have not – Report the Imposter account and warn all the people in your friend list to also report the account.
Some helpful linked from Facebook:
How to fix it
Change your Profile picture and Cover photo, as the fake account is likely to have copied these and is using them. Friends can then distinguish between the imposter and the correct Facebook account.
Check what is on Public View – this is done by choosing the ‘View As’ tab on your Profile Page.
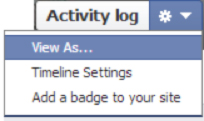
View As Tab – Will display a public view of your Timeline.
Lock down your Friend list. To do this ~ Click the friends tab on your Profile and from the dropdown box choose the option of ‘Edit Privacy’ and then ‘Only Me’.
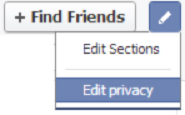
Click on the Friends Tab on your profile – Edit Privacy – Only Me
Friend Hacks
The more difficult issue comes from a friend who appears to have just joined Facebook and sends you a request. Be on alert, verify the account by sending the friend a text message or email. Do Not Send an inbox message to this new account request, as this does not verify the account! If you are not comfortable contacting the person to verify the account, should they really be on your friend list?!
(If you feel you have to friend them, once verified, place them in the ‘Restricted’ or ‘Acquaintance’ listing so they view only a limited profile.)
Some would say the above is too cumbersome and time consuming, but how much is your information worth? Isn’t going the extra yards to protect your account, personal posts and photos worth it?! …. I think so!
Real life scenario
A new person started at the office and you later receive a friend request from them. A check of their Timeline shows their account was only opened last monday. For the moment you ignore the account request. The next day you check the account and they have managed to friend 16 of your mutual friends.
Nobody has bothered to check via text, email or other contact, to verify this person or the account. It is later discovered it is an imposter account.
This ‘friend hack’ now has access to a number of colleagues information from that work environment, along with access to their family photos, friends, other information and personal posts.
This is a real scenario, discovered this week! These work colleagues had no idea and are concerned as their information may have been downloaded, copied, printed out or shared by the fake account!
More than ever being a friend on social media, needs to hold an element of respect, trust and appreciation that you have been chosen to be an online friend.
The friends you have on Facebook need to have your back… if you can’t verify them or trust them.. ‘unfriend’ and get rid of them! This is for online safety and management of your digital reputation, not only for you, but for your family and friends.
 Janita Docherty founder and Director of CyberActive Services is a trained Crime Prevention Executive with more than 18 years experience in the field of law and criminal investigation. Janita specialises in Facebook and Internet Safety instruction and is recognised for her work with law enforcement Units dedicated in the fields of E-Crime, Sex Crime, State Intelligence and Tactical Intelligence areas. Janita has an intricate knowledge on the workings of Facebook from a criminal intelligence perspective and is a leader in her field regarding Facebook training to Police and specialist law enforcement departments both in Australia and the United States. Janita has completed training with the Internet Crime Against Children (ICAC) Taskforce, and holds a number of Certifications, including a Diploma in Frontline Management, a full qualification in Crime Prevention Through Environmental Design (CPTED), is a Youth Mental Health First Aider and has been presented with a National Service Medal. She is held in high regard within social media and law enforcement domains, for her enthusiasm to educate professionals, regarding online safety and digital reputation management.
Janita Docherty founder and Director of CyberActive Services is a trained Crime Prevention Executive with more than 18 years experience in the field of law and criminal investigation. Janita specialises in Facebook and Internet Safety instruction and is recognised for her work with law enforcement Units dedicated in the fields of E-Crime, Sex Crime, State Intelligence and Tactical Intelligence areas. Janita has an intricate knowledge on the workings of Facebook from a criminal intelligence perspective and is a leader in her field regarding Facebook training to Police and specialist law enforcement departments both in Australia and the United States. Janita has completed training with the Internet Crime Against Children (ICAC) Taskforce, and holds a number of Certifications, including a Diploma in Frontline Management, a full qualification in Crime Prevention Through Environmental Design (CPTED), is a Youth Mental Health First Aider and has been presented with a National Service Medal. She is held in high regard within social media and law enforcement domains, for her enthusiasm to educate professionals, regarding online safety and digital reputation management.











 Janita Docherty founder and Director of CyberActive Services is a trained Crime Prevention Executive with more than 18 years experience in the field of law and criminal investigation. Janita specialises in Facebook and Internet Safety instruction and is recognised for her work with law enforcement Units dedicated in the fields of E-Crime, Sex Crime, State Intelligence and Tactical Intelligence areas. Janita has an intricate knowledge on the workings of Facebook from a criminal intelligence perspective and is a leader in her field regarding Facebook training to Police and specialist law enforcement departments both in Australia and the United States. Janita has completed training with the Internet Crime Against Children (ICAC) Taskforce, and holds a number of Certifications, including a Diploma in Frontline Management, a full qualification in Crime Prevention Through Environmental Design (CPTED), is a Youth Mental Health First Aider and has been presented with a National Service Medal. She is held in high regard within social media and law enforcement domains, for her enthusiasm to educate professionals, regarding online safety and digital reputation management.
Janita Docherty founder and Director of CyberActive Services is a trained Crime Prevention Executive with more than 18 years experience in the field of law and criminal investigation. Janita specialises in Facebook and Internet Safety instruction and is recognised for her work with law enforcement Units dedicated in the fields of E-Crime, Sex Crime, State Intelligence and Tactical Intelligence areas. Janita has an intricate knowledge on the workings of Facebook from a criminal intelligence perspective and is a leader in her field regarding Facebook training to Police and specialist law enforcement departments both in Australia and the United States. Janita has completed training with the Internet Crime Against Children (ICAC) Taskforce, and holds a number of Certifications, including a Diploma in Frontline Management, a full qualification in Crime Prevention Through Environmental Design (CPTED), is a Youth Mental Health First Aider and has been presented with a National Service Medal. She is held in high regard within social media and law enforcement domains, for her enthusiasm to educate professionals, regarding online safety and digital reputation management. 