I’m sorry Sir, it’s against the law
There are plenty of arcane, not to say bizarre laws in the UK.
- MPs aren’t aware of wear armour in parliament.
- You can’t beat or shake a carpet rug in any street in the Metropolitan Police District.
- It’s illegal to import Polish potatoes (put on the Statute Book in 2004)
For more examples, see here.
Some of the laws don’t prohibit behaviour but officially sanction it:
Like the right to drive sheep across London Bridge as freemen of the City of London
Or the right for pregnant women to relieve themselves anywhere they see fit.
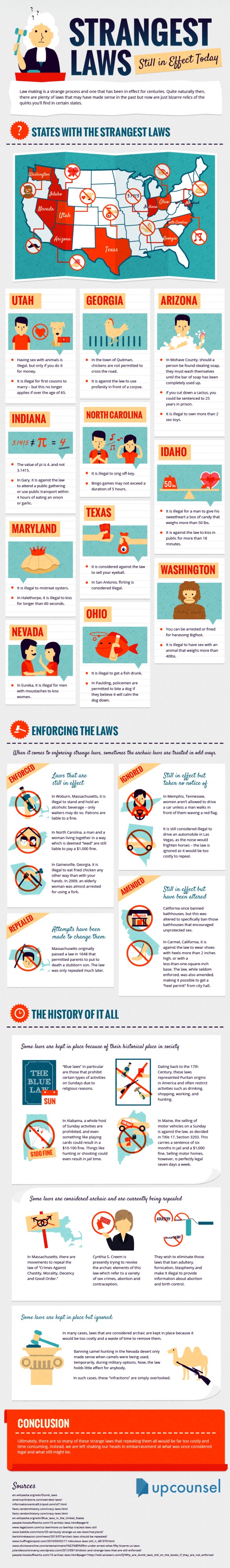
However, as usual, we must acknowledge the superiority of our US friends when it comes to the wild and wacky category:
See the infographic below to find out:



 At last fall’s International Association of Chiefs of Police (IACP) conference, IBM previewed its new i2 Intelligent Law Enforcement offering. Billed as
At last fall’s International Association of Chiefs of Police (IACP) conference, IBM previewed its new i2 Intelligent Law Enforcement offering. Billed as 

