Facebook Secure Browsing for Officer Safety
And the implications for department social media policy
 Early this year Facebook offered users the ability to use the sight a bit more securely with “secure browsing” (https) or SSL encryption, as Facebook said, “whenever possible”. It’s important to enable https, otherwise, any hacker sharing the same public wifi can easily infiltrate your social media accounts. But for police officers concerned about their own privacy and safety, there’s more to it.
Early this year Facebook offered users the ability to use the sight a bit more securely with “secure browsing” (https) or SSL encryption, as Facebook said, “whenever possible”. It’s important to enable https, otherwise, any hacker sharing the same public wifi can easily infiltrate your social media accounts. But for police officers concerned about their own privacy and safety, there’s more to it.
Ethical hacker James F. Ruffer III of Unibox explained that with a plugin like Mozilla Firesheep anyone can BE YOU on sights like Facebook, WordPress, FourSquare, and Twitter The one protection a user has is enabling secure browsing with the https setting. In a recent post on the Social Media Security blog , he explained how with access, a hacker can control every aspect of the victim’s Facebook profile, including the victim’s Facebook Pages. He added, “Once I am in, the victim has to check secure browsing, log out, and log back in,” he said. “That’s the only way to destroy my attack vector.” Firesheep is a Mozilla Firefox browser extension and utilizes packet sniffing methods to intercept unencrypted cookies or sessions.
This technique is known as “sidejacking” and although the hacker doesn’t have control over the victim’s account, they have mirrored what the victim is doing from his or her browser onto theirs. Due to the high level of attention this security flaw demanded, a Mozilla Firefox plugin called Blacksheep was quickly developed to detect if Firesheep is being used on a network, Blacksheep tries to create “false” sessions IDs on a network to see if the sessions are being hijacked.
Hackers can also use Firesheep to extend their access to Social Media Management platforms and still get simultaneous control of all the victim’s profiles from there, even if the https secure browsing is enabled.
Detective Constable and forensics investigator Warren Bulmer of the Toronto Police Service is an expert on Facebook security. He explained in most cases the victim wouldn’t know their account has been compromised unless the hacker makes a change. “As long as the person doesn’t do anything they could spy all day long. They can take digital pictures of your screens and collect intelligence all day long. There’s no way to know that they’re there.”
A big part of the problem is Facebook itself. Its new features are implemented automatically, so that users have to actively change the features, which, in many cases, involve user data. Facebook isn’t trying to allow hacking, rather than allow themselves the ability to collect mass amounts of user data. However, the tactic does leave security holes.
Recently the security firm Sophos issued an open letter to Facebook asking for three things, one of which was for https security to be turned on by default. When Facebook introduced the feature, the social network posted on its blog, “We hope to offer HTTPS as a default whenever you are using Facebook sometime in the future.”
Until Facebook makes secure browsing the default setting, know this:
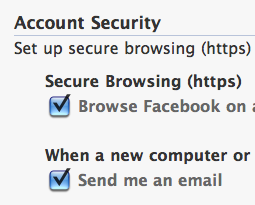
- To turn on https secure browsing, in the upper right corner pull-down menu, go to “Account Settings”, then “Account Security”. The https checkbox is the first option.
- Some games you play or applications that you might install will turn off https. You should be notified when this happens, be sure to re-enable secure browsing afterwards.
- With https security turned on, your use of Facebook will likely run more slowly. It’s a small price to pay.
- Never trust any social network to guard your privacy. Guarding your information and therefore your safety and career security is your responsibility.
Regardless of whether Facebook enables the security setting by default or not, law enforcement officers need to take extra care to secure their profiles. Ruffer recommends using an Ironkey, an inexpensive USB device that guarantees secure browsing. Secure data plans like 3G, or a portable hub such a Verizon’s “Mifi”, can be pricey, but may be the best option. Otherwise, avoiding public wifi is the best protection.
Bulmer cautions that there are things you should “just not do” from a public computer or on a public wifi. “In these Internet cafés or coffee shops, you have no idea what their network or someone else also using it is capturing. It would be nice to be able to say the restaurant or hotel is legit and they don’t keep information. The reality is, you really don’t know that. The safest method, if you really need to use these social networks is to do as much security as possible,” he said.
So what should this mean for department social media policy?
When someone leaves the department, does department policy spell out how their accounts are processed and closed so that any security breaches that may have taken place on those accounts are done away with? The first article on ConnectedCOPS.net was an article on social media policy for law enforcement in August of 2009. In it, I called for requiring the people who use social media representing the department or in their personal lives to be competent with regard to how the platforms work. Social media is like anything else a law officer does at work, and it requires a significant amount of training to ensure this competence. Security issues like the one illustrated here reinforce the importance of this point. To this end, department policy should also require the pertinent security measures to help keep these breaches from happening in the first place.



